Unleash AI Detection Bypass Power
Gain an edge with our AI detection bypass tool, ensuring seamless and effective operation.
Maximize Your AI Detection Power
Enhanced Detection
Stay ahead with our advanced AI detection capabilities for reliable and accurate results.
Effortless Bypass
Easily bypass AI detection barriers with our intuitive and efficient tool.
Seamless Operation
Experience smooth and uninterrupted operation with our AI detection bypass solution.
How to use AI Content Detector
- 1
Choose a template
Select the necessary template from the template gallery.
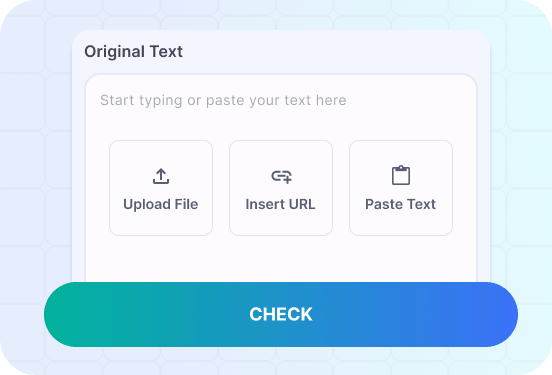
- 2
Provide more details
Fill out the carefully selected inputs to create the best quality of output content.
- 3
Enjoy the results
Copy, save for later, rate the output or hit regenerate button.
