AI Bypass Detection: Uncover Deceptive Tactics
Detect and prevent AI bypass tactics with our advanced detection technology for a secure and trustworthy environment.
Enhanced AI Bypass Detection
Advanced Threat Detection
Identify and counter sophisticated AI bypass methods with real-time advanced threat detection.
Customizable Security Measures
Tailor security measures to your specific needs and stay ahead of deceptive AI tactics.
Seamless Integration
Easily integrate our AI bypass detection technology into your existing systems for immediate protection.
AI Bypass Detector: Protecting Your Security and Privacy
Real-Time Threat Detection
AI Bypass Detector offers real-time threat detection, continuously monitoring for any attempts to bypass security measures or invade privacy. By leveraging advanced AI algorithms, it provides proactive protection against evolving threats.
The system swiftly identifies suspicious activities and potential breaches, allowing for immediate action to be taken to safeguard sensitive data and prevent unauthorized access.
Try Justdone ->
Enhanced Privacy Measures
With AI Bypass Detector, users benefit from enhanced privacy measures that block unauthorized attempts to bypass security protocols. It ensures that personal and confidential information remains secure, reducing the risk of data breaches and identity theft.
The tool strengthens the security infrastructure, enabling individuals and businesses to maintain the integrity of their digital assets in an increasingly connected environment.
Try Justdone ->
Seamless Integration and User-Friendly Interface
The AI Bypass Detector seamlessly integrates into existing security frameworks, offering a user-friendly interface for easy management. Its intuitive design and compatibility with various platforms make it a valuable addition to any cybersecurity strategy.
Users can efficiently navigate the system, accessing comprehensive security insights and alerts to stay informed and in control of their digital protection.
Try Justdone ->
Maximizing Security with AI Bypass Detector
Regular System Updates
Regularly updating the AI Bypass Detector ensures that the latest security patches and threat intelligence are applied, bolstering the overall protection against evolving bypass techniques and privacy breaches.
By staying current with updates, users can mitigate potential vulnerabilities and optimize the system's effectiveness in safeguarding sensitive data.
Customized Security Settings
Tailoring the security settings of AI Bypass Detector to align with specific user requirements enhances the precision of threat detection and privacy protection. Custom configurations enable targeted defense against potential bypass attempts and unauthorized access.
By optimizing the settings, individuals and organizations can adapt the tool to suit their unique security needs, ensuring a personalized and robust defense mechanism.
Educational Resources and Training
Utilizing the educational resources and training materials provided for AI Bypass Detector empowers users to maximize their understanding of potential threats and effective utilization of the tool's security features.
By investing in ongoing education, individuals and teams can elevate their cybersecurity awareness, enabling proactive measures to counter bypass attempts and protect privacy.
Multi-Layered Authentication
Implementing multi-layered authentication processes in conjunction with AI Bypass Detector fortifies the defense against unauthorized access and potential security breaches. By incorporating additional verification steps, users add an extra layer of protection to their accounts and sensitive data.
By leveraging multi-factor authentication, individuals can significantly reduce the risk of bypass attempts and enhance the overall security posture.
Incident Response Planning
Developing a comprehensive incident response plan that includes the integration of AI Bypass Detector enables swift and effective mitigation of security incidents. By outlining predefined protocols and actions, organizations can streamline their incident response efforts and minimize the impact of potential bypass attempts.
By proactively preparing for security incidents, businesses can leverage the capabilities of the AI Bypass Detector to enact timely and decisive measures in the event of a breach.
How to use AI Content Detector
- 1
Choose a template
Select the necessary template from the template gallery.
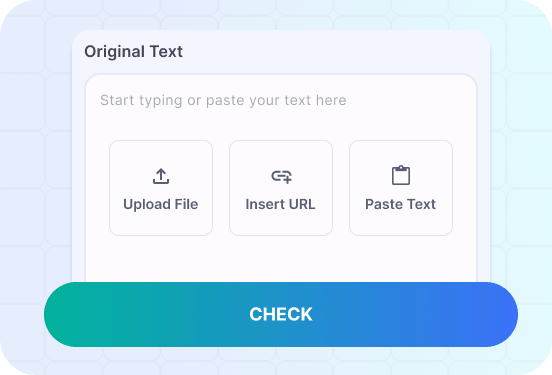
- 2
Provide more details
Fill out the carefully selected inputs to create the best quality of output content.
- 3
Enjoy the results
Copy, save for later, rate the output or hit regenerate button.

Unveiling AI Bypass Detector in Action
Explore practical examples of how AI Bypass Detector responds to security challenges and safeguards privacy in various scenarios.
Craft a convincing email to entice users to disclose their login credentials, and demonstrate how AI Bypass Detector identifies and mitigates the threat.
As a reputable financial institution, we understand the importance of safeguarding your account information. Please verify your credentials by clicking the link below to ensure uninterrupted access to your account.
AI Bypass Detector swiftly analyzes the email content and detects the suspicious request for credential verification. Upon recognizing the phishing attempt, the system triggers an alert, notifying the user of the potential threat and advising against interacting with the fraudulent link.
The advanced algorithms of AI Bypass Detector meticulously assess the email's characteristics, identifying key indicators of phishing tactics and preventing unauthorized access to sensitive login credentials. By proactively intercepting such threats, the tool effectively safeguards users from falling victim to phishing attacks.
Create a scenario where an unauthorized user attempts to access confidential company data and demonstrate how AI Bypass Detector detects and prevents the breach.
An unauthorized attempt to access sensitive company data has been identified. Please provide your login credentials to verify your access permissions and proceed with viewing the content.
Upon the unauthorized login attempt, AI Bypass Detector immediately triggers an alert, notifying the system administrator of the potential security breach. The tool swiftly blocks the unauthorized access attempt, preventing the exposure of confidential company data to unauthorized individuals.
Utilizing its advanced threat detection capabilities, AI Bypass Detector analyzes access attempts in real time, identifying discrepancies and unauthorized activities to proactively mitigate security risks. By swiftly responding to unauthorized access attempts, the tool reinforces the security posture of the company's digital assets, ensuring the protection of sensitive information.